In today's world, data encryption is not just a whim, but a direct necessity. In particular, encrypting http traffic is of great importance for all sites where any personal data is processed. And also to protect against mitm attacks.
Thus, the use of Forward Secrecy on web servers becomes mandatory for each site that works using the https protocol and allows you to improve the strength of information encryption.
Forward secrecy can be properly configured in nginx.
Suppose you have a site that needs to support https work. First of all you need to create a Diffie-Hellman key.
# openssl dhparam -out /etc/nginx/ssl/dh-2048.pem 2048
And set the appropriate access rights for it.
# chmod 0600 /etc/nginx/ssl/dh-2048.pem
Next you need to configure nginx. Here is an example configuration for a site running ssl.
server {server_name example.com; listen 80; listen 443 ssl; ssl_certificate /etc/nginx/ssl/example.com_crt.pem; ssl_certificate_key /etc/nginx/ssl/example.com_key.pem; ssl_dhparam ssl / dh-2048.pem; ssl_ciphers ECDH: DH:! ADH:! AECDH:! SEED:! DES:! 3DES:! RC4:! NULL; ...} Consider each variable.
ssl_dhparam - the path to the file with the Diffie-Hellman key. You can specify the path relative to the directory with the nginx configuration files.
ssl_ciphers - ciphers to be used for ssl connections. I have ciphers selected for prosody . The minimum key length is 128 bits. All support forward secrecy.
After configuring nginx, restart with the service nginx restart command.
To test the settings, use the https://www.ssllabs.com/ssltest/index.html service. In the test results, in the paragraph “Protocol Details”, there should be such a result:
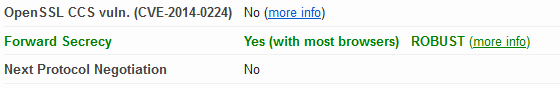

What about backward compatibility?
I recommend this set: ECDH: DH: EECDH: + AES256: -3DES: RSA + AES: RSA + 3DES:! NULL:! RC4;