OpenVPN is a software package that allows you to protect user traffic from “interception” by providing encrypted data transmission from the client’s device to the server with OpenVPN installed. Great for using public wifi access points where information can be intercepted by third parties. Or in the case when your ip is blocked on a certain site and you need to safely bypass this restriction.
In addition to installing and configuring OpenVPN on the server, you must be able to configure the client for access from a computer where Windows will be used as the operating system.
Using the standard package manager, install openvpn.
# aptitude install openvpn
The content of the article:
- Создание сертификатов 1 Creating Certificates
- Настройка сервера 2 Server Setup
- Перенаправление трафика через OpenVPN 3 Redirecting traffic through OpenVPN
- OpenVPN клиент на Windows 4 OpenVPN client on Windows
- OpenVPN совместно с NetworkManager 5 OpenVPN with NetworkManager
Creation of certificates
OpenVPN necessarily requires the generation of certificates for the server and clients. This is logical, because the connection from the client to the server must be encrypted.
Navigate to the openvpn folder:
# cd / etc / openvpn
We will generate keys using easy-rsa.
Create a folder with configuration files and links to certificate generation scripts:
# make-cadir rsa # cd rsa
Open the vars configuration file and change the parameters:
export KEY_COUNTRY = "US" export KEY_PROVINCE = "CA" export KEY_CITY = "SanFrancisco" export KEY_ORG = "Fort-Funston" export KEY_EMAIL = "me@myhost.mydomain"
KEY_COUNTRY - enter the country code (RU, UA, etc.);
KEY_PROVINCE - this item is not relevant if you do not live in the United States. :) You can replace the XX;
KEY_CITY - your city where you live;
KEY_EMAIL - your email address.
And also uncomment the export KEY_CN line, for the value for which specify the server name:
export KEY_CN = "example.com"
All variables are filled in Latin.
Save the file and run it:
# vars
Then start deleting old certificates:
# ./clean-all
Create a root certificate:
# ./build-ca
If, when generating the root certificate, you get the error error:0E065068:configuration file routines:STR_COPY:variable has no value:conf_def.c:618:line 198 , add the line to the vars file:
export KEY_ALTNAMES = "something"
And then re-run the previous commands:. vars, ./clean-all, ./build-ca.
The next step is to create a key and server certificate.
# ./build-key-server server
Then create a certificate and key for the client:
# ./build-key client
Please note: for each client you should generate your own certificate and key. You just need to specify different names (instead of the client) and change the paths to them in the configuration files. At the same time, you can protect clients' keys with a password; for this, use the command build-key-pass instead of build-key.
Next, you need to create a Diffie-Hellman key to be able to use Forward Secrecy:
# ./build-dh
And the key for tls authentication:
# openvpn --genkey --secret /etc/openvpn/ta.key
Now you need to copy the server certificates and keys to the OpenVPN settings folder:
# cp keys / ca.crt keys / server.crt keys / server.key keys / dh2048.pem / etc / openvpn /
And also put on them the rights that allow reading and changing only for their owner.
# chmod 0600 /etc/openvpn/ca.crt /etc/openvpn/server.crt /etc/openvpn/server.key /etc/openvpn/dh2048.pem /etc/openvpn/ta.key
Be sure to copy to your computer, for example, the desktop, from the keys folder, the keys necessary for connecting the client: client.crt , client.key , ca.crt , ta.key .
This completes the certificate preparation process.
Server Tuning
In the / usr / share / doc / openvpn / directory there is an example file for setting up an Openvpn server. Copy it to the / etc / openvpn / directory and unzip:
cd / etc / openvpn; cp /usr/share/doc/openvpn/examples/sample-config-files/server.conf.gz / etc / openvpn /; gunzip server.conf.gz
Now we will consider the necessary parameters for openvpn to work.
The port on which Openvpn will accept connections. By default, 1194. I recommend to change it in order to conceal it. You can even disguise openvpn under a Web-server, specifying port 80.
port 20100
Register paths to certificate files and server key.
ca ca.crt cert server.crt key server.key
The path to the key Diffie-Hellman.
dh dh2048.pem
Both paths relative to the / etc / openvpn directory (if files are located in it) and absolute can be specified.
Find and uncomment the line:
push "redirect-gateway def1 bypass-dhcp"
It is needed to be able to access the Internet through the OpenVPN server. If it is not uncommented, only computers within the network will be available.
You also need to specify the DNS servers for connecting clients.
push "dhcp-option DNS 213.183.57.55" push "dhcp-option DNS 87.98.175.85"
Depending on the location of the server, you can pick up other dns-servers, for example, on the project OpenNIC .
Next, find and uncomment the tls-auth parameter.
tls-auth ta.key 0
Attention! In the client settings, the last digit of this parameter should be replaced by 1 - tls-auth ta.key 1 .
Just below in the configuration file follows the listing of available ciphers. Uncomment the AES-128-CBC cipher.
cipher AES-128-CBC # AES
If necessary, it can be replaced with AES-256-CBC . In the client's configuration file, the cipher must be identical to the server cipher.
Also add the auth parameter. By default, 160-bit sha1 keys are used for authentication, but the sha1 algorithm is recognized as vulnerable. When specifying the following parameter, SHA512 keys with a length of 512 bits will be used.
auth SHA512
As well as the parameter tls-version-min, which determines the version of tls used. In this case, the latest version is 1.2. Attention! Network Manager does not support (at the time of writing) this parameter. Therefore, if you plan to connect to the VPN server through the Network Manager, then this parameter is NOT specified in the server settings.
tls-version-min 1.2
OpenVPN should not be run as root. Therefore, uncomment the lines:
user nobody group nogroup
It will not be superfluous to enable logs for OpenVPN. Especially, at first use after tuning for searching for errors, etc.
log /var/log/openvpn.log
Leave all other parameters of the /etc/openvpn/server.conf configuration file with default values. This completes the OpenVPN server setup.
Activate openvpn with the command:
# systemctl enable openvpn
And restart:
# service openvpn restart
It is also useful to check the log for errors.
Redirect traffic through OpenVPN
To be able to access the Internet through the server openvpn, you need to do something for this.
1. Configure sysctl
In the console, run the command:
# sysctl net.ipv4.ip_forward
If the output of the command is equal to net.ipv4.ip_forward = 1 , then there is no need to change anything. If the value of the variable is 0, then the following line should be added to the /etc/sysctl.conf file:
net.ipv4.ip_forward = 1
And reload the rules with the command:
# sysctl -p
2. Configure iptables
Alternately, run the following commands in the console:
# iptables -A FORWARD -i eth0 -o tun0 -m state --state ESTABLISHED, RELATED -j ACCEPT # iptables -A FORWARD -s 10.8.0.0/24 -o eth0 -j ACCEPT # iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -o eth0 -j MASQUERADE
Thus, we will allow traffic through the OpenVPN server for subnet 10.8.0.0 within the limits of already established connections.
If the openvpn client needs to assign a specific external ip address of the server, then instead of the last command from the list of previous ones for iptables, you need to run this:
-A POSTROUTING -s 10.8.0.0/24 -o eth0 -j SNAT --to-source 127.0.0.1
Where after the parameter –to-source, you should specify the external ip server.
OpenVPN client on Windows
Getting started setting up an Openvpn client on Windows. Everything is simple here: download the client from the official site, install, create the configuration file and launch it.
It should be noted that it is necessary to start openvpn on Windows with the rights of the administrator if control of accounts is active.
If you did not change the installation path, then the examples of the configuration files on your PC are located in the C: \ Program Files \ OpenVPN \ sample-config directory. Copy the client.ovpn file from here and place it in the C: \ Program Files \ OpenVPN \ config directory.
Remember the certificates created for the client? They should also be downloaded from the server and copied to this directory.
Open the client.ovpn configuration file and find the remote my-server-1 1194 parameter. Instead of my-server, specify the ip or domain name of your server. Then the port that we changed earlier. As a result, the line may look like this:
remote 192.168.0.1 20100
Next, you need to specify the path to the certificates that you generated on the server. For each client, a key is created with a unique name, which should be indicated below, instead of client .
ca ca.crt cert client.crt key client.key
You should also uncomment the parameter that specifies the path to the tls-key.
tls-auth ta.key 1
Earlier it was already said that the last digit on the server should be 0, on the client - 1.
And the last parameters are ciphers that you installed on the server.
cipher AES-128-CBC auth SHA512 tls-version-min 1.2
This is all that is required to configure the client. Try running the OpenVPN client and connect to your server. The necessary connection information will be displayed in the openvpn gui window.
OpenVPN with NetworkManager
Install the graphical interface for the Network Manager.
# aptitude install network-manager-openvpn-gnome
And restart.
# service network-manager restart
We copy the certificates generated for the client into an arbitrary folder on the computer. For example, in /home/user/.openvpn/.
Click the right mouse button on the network manager icon, select the item “change connections”, add a new connection of the type “OpenVPN”.
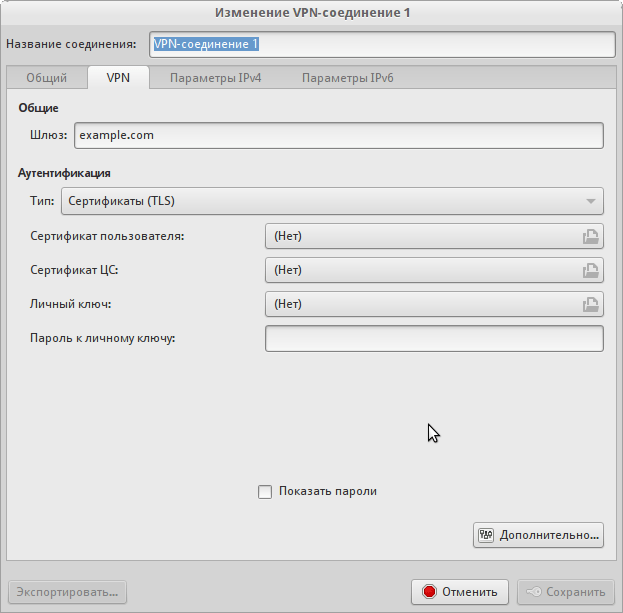
Specify:
- Connection name
- Gateway (domain or server ip)
- Type: Certificates
User certificate is a certificate that we generated at the beginning for the client (client.crt).
CA certificate - ca.crt file.
The private key is the client's key (client.key).
Click on the "Advanced" button. In the window that opens, in the "General" tab you will need to change a few items.
- Use a different gateway port (if you specified a non-standard when setting up the server)
- Use lzo compression
Switch to the "Security" tab. Select the cipher, as in the server settings. As the value of the hmac authentication parameter, you should specify an algorithm, as in the auth value of the server. In the article we chose SHA512.
Open the TLS Authentication tab and tick the following items:
- Verify peer ...
- Use additional TLS authentication
For the last parameter, specify the path to the ta.key file, and select 1. as the key direction from the drop-down list. Similarly to the configuration file for Windows.
Save the connection and try to connect. :)
Just in case, we look that NM writes when connecting to the system log:
# tail -f / var / log / syslog

Thank you for the article. Very helpful.
Excellent article, author dear person!
An author like I did not try to debug to understand why my clients cannot connect, openvpn does not make logs! tell me what to do!
So you need to check the logs of clients. OpenVPN GUI such log necessarily leads. Right click -> show log.
Maybe an item is missing from the instructions ...
Thanks, but as it turned out, it was necessary to do so #openvpn /opt/vp/vp.conf and the application hooked up the config file - the logs went - I looked at everything and made the vpn a worker.
Conscious manualbook author ask you. How to make a tunnel between the server on Debian and Mikrotikom. Connect their local network. 2 apartments.
Thanks for the post. Still interested in setting up mobile clients, such as here - http://sysadm.pp.ua/linux/shifrovanie/openvpn-client-server.html . Can you please advise a good and convenient mobile OpenVPN client?
On my Android smartphone, I use the official client from the developer Openvpn - “Openvpn connect” https://play.google.com/store/apps/details?id=net.openvpn.openvpn
It is quite easy to set up. The generated files for the client must be uploaded to any folder on the phone’s flash drive. Then run Openvpn Connect, select “Import” in the menu, then “Import Profile from SD card”. The file manager will open, where you need to select the * .ovpn file, click on the “Select” button. In confirmation of successful import, the message “Profile imported” is displayed on the screen.
To connect, press the "Connect" button. That's all. :)
I do not know about other clients, but this one works great.
PS If you plan to connect simultaneously from a computer and from a phone, then for the latter you should generate your own key and certificate.
The article helped to understand the principles of openvpn in general. Thank.
SUCTION AND DOES NOT WORK ON THIS INSTRUCTION NIFIGA!
Thank. Everything is working!
upd.
Clause 2 decided to install the rights to the client.key key (apparently overlooked it first). + it was necessary to set the TCP connection type explicitly and specify the adapter type - TAP / TUN
Thank! Great article!
I set everything up according to the instructions, but there is such a problem:
The client connects to the server, but there is no Internet. The client pings both the VPN 10.8.0.1 server and the dedicated server ip. From the server itself, external sites respond without problems. It turns out that the dog is buried somewhere in the IPtables and ip.frwarding. Any thoughts? Can that quickly advise than to deal with this forest?
It is necessary to prescribe other routing rules
iptables -t nat -A POSTROUTING -o venet0 -j SNAT —to IP_ADDRESS_Your_SERVER
iptables -A FORWARD -i venet0 -o tun0 -m state —state RELATED, ESTABLISHED -j ACCEPT
iptables -A FORWARD -i tun0 -o venet0 -j ACCEPT