In the case of a server hacking, a hacker can modify the files in order to leave some backdoor, shell, etc. The modified files could be tracked by the modification date, but this date can be easily forged through the touch utility.
Instead you can compare file checksums. If the checksum of the file is different from the existing one, the file has been modified. This method can be used for any files: configuration files, site files, executable files, etc.
To calculate the checksums of files, for example, in the / etc folder, we use the combination of the find and sha256sum commands:
# find / etc -type f | xargs sha256sum> file.txt
The -type f flag tells find to search for files only (for folders it is impossible to calculate the checksum), and file.txt is the name of the file where the hash sums of all found files will be written.
If it is necessary to calculate the checksum only for certain files, php, for example, then the -name \ *. Php flag should be specified (the file mask * must be escaped with a backslash):
# find www -type f -name \ *. php | xargs sha256sum> file.txt
You can also calculate the checksum for a specific file:
# sha256sum backup.tar.gz> file.txt
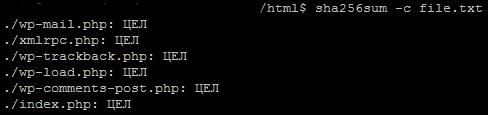
Now compare the hash sums with the hash sums of the files:
# sha256sum -c file.txt
And if the checksum of a specific file coincides with that in file.txt, then this file has not been changed since the last check. The integrity is indicated by the TARGET tag opposite the file.
Of course, this does not help you protect the server, but will provide additional assistance in finding traces of hacker presence.
In addition to sha256, you can use any other algorithm: md5, sha512, sha1, sha384.
